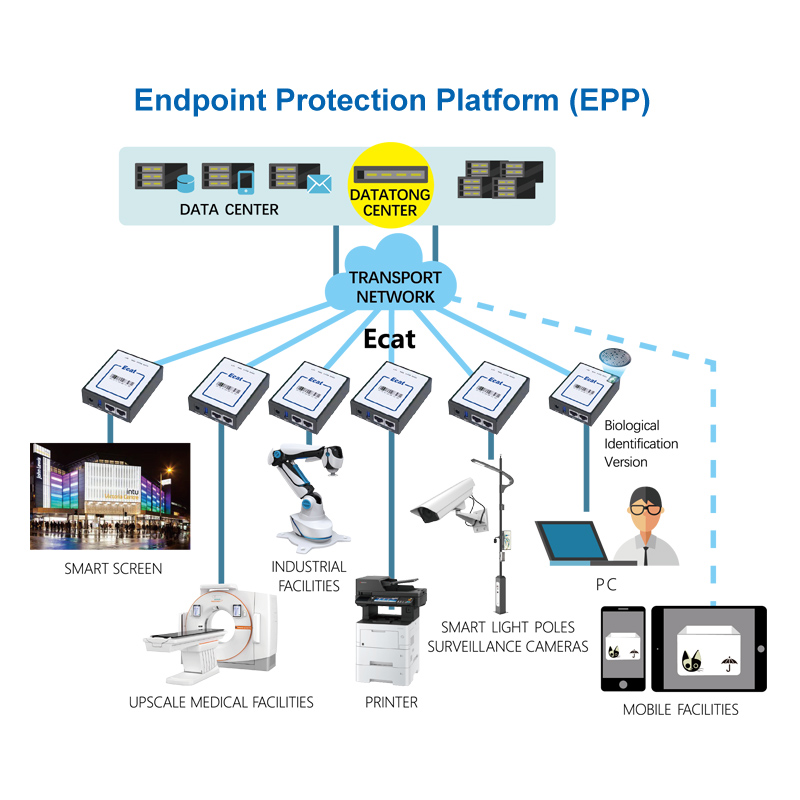
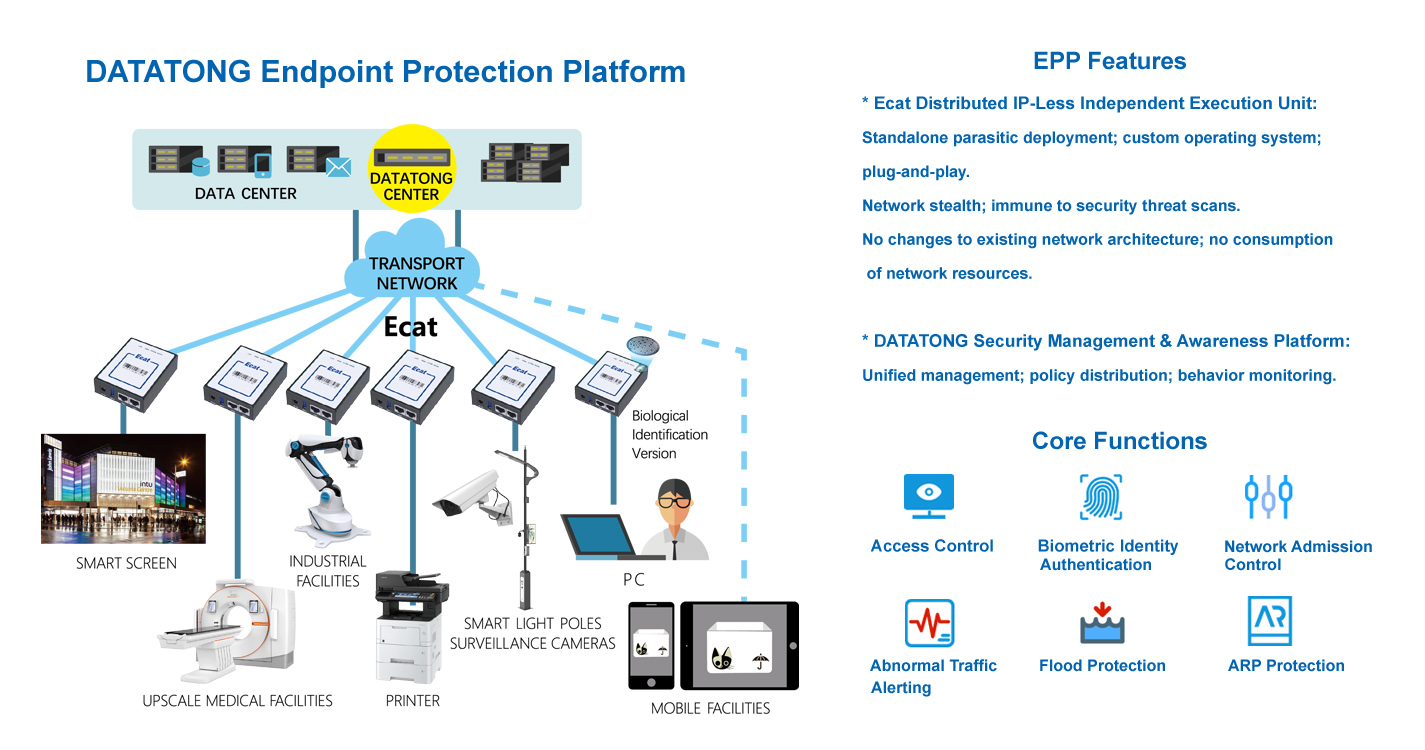
Ecat, an essential part of DATATONG Endpoint Protection Platform, is a revolutionary, IP-less security execution unit that delivers one-to-one, hardware-enforced protection for critical endpoints—acting as an “invisible shield” against cyber threats. Designed to address the biggest pain points of IoT and industrial security (e.g., outdated devices unable to run antivirus software, lateral virus spread, and network exposure), it provides physical isolation, bidirectional threat blocking, and “work while sick” functionality—all without altering endpoint hardware, software, or user workflows. Ideal for medical devices, industrial machinery, and remote infrastructure, Ecat is the frontline defense that keeps endpoints secure and operational.